最近有了新的比特币加密勒索病毒,文件内容为:
====== Attention! ====== All your files, documents, photos, databases and other important files are encrypted and have the extension: 3FB27E87-5A65-684C-C56C-91BB59DFC0B8 You are not able to decrypt it by yourself! The only method of recovering files is to purchase an unique private key. Only we can give you this key and only we can recover your files. To be sure we have the decryptor and it works you can send an email drogo@tfwno.gf (reserve drogo10@protonmail.com) and decrypt one file for free. But this file should be of not valuable! Do you really want to restore your files? Write your rersonal ID to email drogo@tfwno.gf Your personal ID: 3FB27E87-5A65-684C-C56C-91BB59DFC0B8 Attention! * Do not rename encrypted files. * Do not try to decrypt your data using third party software, it may cause permanent data loss. * Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
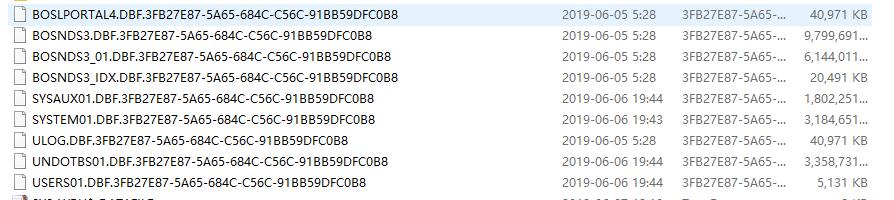
加密之后文件为:
我们通过数据库层面恢复,可以open数据库,然后使用exp/expdp导出数据,实现恢复之后,数据库直接可以使用