在查看一网友alert日志时发现很多ORA-00600[kgscLogOff-notempty]记录,通过查询MOS分析记录结果如下:
alert日志出现ORA-00600[kgscLogOff-notempty]
Wed Aug 1 10:28:35 2012 Errors in file /vgdata/oracle/admin/orcl1/udump/orcl1_ora_18430.trc: ORA-00600: internal error code, arguments: [kgscLogOff-notempty], [1], [], [], [], [], [], [] Wed Aug 1 10:28:38 2012 Errors in file /vgdata/oracle/admin/orcl1/udump/orcl1_ora_18508.trc: ORA-00600: internal error code, arguments: [kgscLogOff-notempty], [3], [], [], [], [], [], []
trace结合MOS分析原因
Oracle Database 10g Enterprise Edition Release 10.2.0.1.0 - 64bit Production
With the Partitioning, OLAP and Data Mining options
ORACLE_HOME = /vgdata/oracle/product
System name: HP-UX
Node name: hpdc1
Release: B.11.31
Version: U
Machine: ia64
Instance name: orcl1
Redo thread mounted by this instance: 1
Oracle process number: 230
Unix process pid: 18430, image: oracleorcl1@hpdc1
*** SERVICE NAME:(orcl1) 2012-08-01 10:28:35.937
*** SESSION ID:(191.141) 2012-08-01 10:28:35.937
*** 2012-08-01 10:28:35.937
ksedmp: internal or fatal error
ORA-00600: internal error code, arguments: [kgscLogOff-notempty], [1], [], [], [], [], [], []
----- Call Stack Trace -----
calling call entry argument values in hex
location type point (? means dubious value)
-------------------- -------- -------------------- ----------------------------
ksedst()+64 call _etext_f()+23058430 000000000 ? 000000001 ?
09017233648
ksedmp()+1680 call _etext_f()+23058430 000000000 ?
09017233648 C000000000000D20 ?
40000000052C8C90 ?
000000000 ? 000000000 ?
000000000 ?
ksfdmp()+48 call _etext_f()+23058430 000000003 ?
09017233648
kgerinv()+400 call _etext_f()+23058430 40000000093F4370 ?
09017233648 000000003 ?
C000000000000612 ?
000008F07 ? 000000000 ?
000000000 ?
kgeasnmierr()+144 call _etext_f()+23058430 6000000000015190 ?
09017233648 6000000000016248 ?
6000000000013770 ?
600000000009C808 ?
60000000000165B0 ?
$cold_kgscLogOff()+ call _etext_f()+23058430 6000000000015190 ?
144 09017233648 9FFFFFFFBF562160 ?
9FFFFFFFBF562170 ?
60000000000165C0 ?
000000000 ? 000000001 ?
kkslof()+320 call _etext_f()+23058430 6000000000015190 ?
09017233648
opifcs()+592 call _etext_f()+23058430 C000000360365908 ?
09017233648 C000000000000E21 ?
4000000002E1BF20 ?
000000000 ? 000000000 ?
ksuxds()+1568 call _etext_f()+23058430 C000000360365908 ?
09017233648 4000000002EBA7A0 ?
000008F9F ? 000004810 ?
9FFFFFFFBF56BEF6 ?
C000000360365908 ?
4000000001354140 ?
00000003F ?
ksudel()+128 call _etext_f()+23058430 60000000000A7B54 ?
09016643752 60000000000A7CF8 ?
9FFFFFFFFFFF6C20 ?
600000000009D8A0 ?
opilof()+3664 call _etext_f()+23058430 60000000000A7B54 ?
09016643752 60000000000A7CF8 ?
4000000003D681E0 ?
C00000000000122A ?
00000814F ?
60000000000A7CE0 ?
opiodr()+2016 call opilof()+3664 60000000002BE7B0 ?
60000000002BE7B8 ?
000000001 ?
9FFFFFFFFFFF71B0 ?
600000000009D8A0 ?
60000000002BE7E0 ?
ttcpip()+1824 call _etext_f()+23058430 60000000000AA0BC ?
09017243504 000000001 ?
6000000000015310 ?
6000000000015310 ?
9FFFFFFFFFFF8250 ?
600000000009D8A0 ?
9FFFFFFFFFFF8250 ?
6000000000020D88 ?
opitsk()+2224 call _etext_f()+23058430 6000000000020D80 ?
09017192128 9FFFFFFFFFFFA3D4 ?
6000000000020EE8 ?
000000001 ?
9FFFFFFFFFFFAA90 ?
9FFFFFFFFFFFA884 ?
6000000000020E88 ?
000000000 ?
opiino()+2144 call _etext_f()+23058430 000000000 ? 000000000 ?
09016681384 600000000009D8A0 ?
4000000002AE7E10 ?
000008001 ?
9FFFFFFFFFFFA874 ?
opiodr()+2016 call _etext_f()+23058430 00000003C ?
09016681384 9FFFFFFFFFFFF260 ?
9FFFFFFFFFFFF250 ?
9FFFFFFFFFFFBF90 ?
0000000B0 ?
600000000008F560 ?
opidrv()+1136 call _etext_f()+23058430 60000000000AA0BC ?
09017243504 000000001 ?
6000000000015310 ?
6000000000015310 ?
9FFFFFFFFFFFCAE0 ?
600000000009D8A0 ?
sou2o()+240 call 9fffffffffffcae0 00000003C ? 000000004 ?
9FFFFFFFFFFFF250 ?
opimai_real()+480 call 9fffffffffffcae0 9FFFFFFFFFFFF270 ?
00000003C ? 000000004 ?
9FFFFFFFFFFFF250 ?
main()+352 call 9fffffffffffcae0 000000000 ?
9FFFFFFFFFFFF2A0 ?
main_opd_entry()+80 call 9fffffffffffcae0 000000002 ?
9FFFFFFFFFFFF750 ?
C000000000033910 ?
000000000 ?
--------------------- Binary Stack Dump ---------------------
通过查询MOS发现ORA-600 [kgscLogOff-notempty] On Session Logoff [ID 413120.1]中记录有
The following error may occur on session logoff ORA-600 [kgscLogOff-notempty], [1] or ORA-600 [kgscLogOff-notempty], [2] with a Call Stack like: ... kgscLogOff kkslof opifcs ksuxds ksudel ...
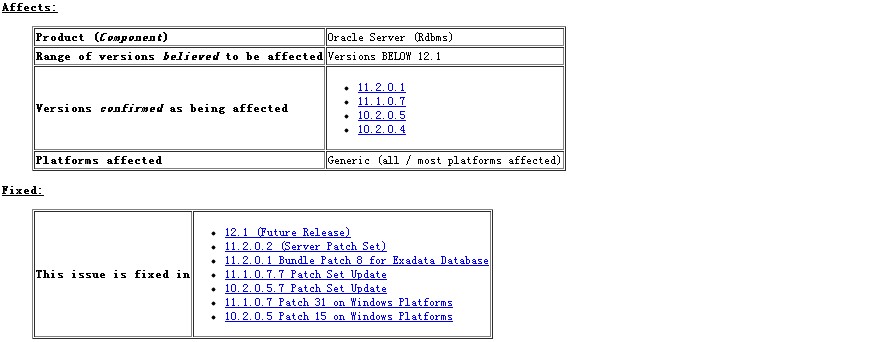
和该数据库中的Stack Dump记录一致,数据库版本也在该bug范围内,从而可以确定是unpublished Bug 4887675
解决方案
该错误是在logoff时产生,对数据库影响不大,如果偶尔出现可以忽略,出现频率过高,建议按照下列方法解决
There is No Data Corruption (or) Data Loss due to this Error. This error occurs during the logoff operation, hence the impact should be negligible. This is fixed in 10.2.0.4 and above releases. One-off patches may be available depending on your current release and operating system. To obtain a patch from MetaLink: 1) Click on Patches. 2) Click on Simple Search 3) Enter patch number: 4887675 4) Select your O/S 5) Click Go. As workaround, avoid Killing/Terminating the Session Abnormally.